Software either is or will be vulnerable. It’s rare that you won’t have to update out-of-date, unsupported or end-of-life software. If your job description involves software or IT asset management (SAM/ITAM), this is part of your day-to-day and nothing particularly out of the ordinary. Then add onto those updates the fact that hackers are regularly attempting to find holes in your software to slip in a malicious attack. This is when your day-to-day gets a bit more interesting and, in some cases, more concerning.
If vulnerabilities are just a part of owning and deploying software, why should they be concerning when we know we can remediate?
Vulnerabilities can cost organizations millions of dollars per breach. Every time a vulnerability is exploited, it exposes valuable data—think Equifax in 2017 or Capital One in 2019—and that not only leads to expensive remediation, but includes costs to those whose data has been affected (the user and personal data, for example, shared for malicious purposes).
Many organizations understand, in the general sense, that vulnerability awareness is key to avoiding those costly breaches. But in practice, countless businesses still don’t have structure and protocols in place to reduce and remediate vulnerabilities that can and will affect their organization. A gap still remains between detection and remediation. This gives hackers more than enough time to take advantage of holes in your IT organization.
Shouldn’t our security team be on top of this?
Yes. And in some cases they’re right on top of the ones that affect your organization. The problem is that there are more than 13,000 vulnerabilities Flexera has detected with vendors and products present in our customers’ environments. Metaphorically speaking, that’s a lot of windows for hackers to climb through and steal valuables.
With so many vulnerabilities out there, even the best security teams need to prioritize. In those cases, teams are often focusing on the highly critical products and their vulnerabilities that are integral to their organization—the mainstay applications that cannot afford the risk or are used so widely that the effect would be disastrous.
But security can’t catch everything.
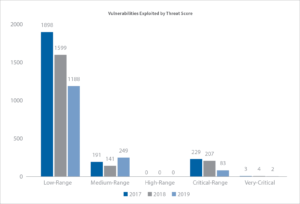
In the latest Flexera Vulnerability Review 2020 report, it was found that the majority of vulnerabilities exposed had low-range threat scores—Flexera’s own scoring of those actually being exploited in the wild—and that many programs miss these exploits when focusing on highly to extremely critical threat scoring.
What can ITAM/SAM do about this if it’s a security issue?
More than you’d think—ITAM, and by extension SAM, are responsible for knowing the assets the organization deploys. It goes a step further in that these initiatives now have security data right alongside their asset data to understand where a vulnerability might be located.
Information Security (InfoSec) content brings together information that both ITAM and security operations find necessary to root out these exposures, including advisory content and threat scoring, from Flexera’s Secunia Research team.
With data from the most reliable resource, delivering the world’s best software vulnerability intelligence, ITAM professionals and teams have the capacity to now assess their IT assets against not only data from the National Vulnerability Database (NVD), but the deep details and consistency of a trusted vulnerability rating built into advisories assigned and defined by Secunia.
Software Vulnerability Management
The way to beat software vulnerabilities is to stay ahead of them. Addressing windows of risk is critical for reducing the odds of attacks and staying secure.
OK, I know how vulnerable my assets are. What do I do with this newfound power?
Now’s the chance to work with your overwhelmed security team and let them know you’ve got their back. Whether you explore the aggregate dataset and drill down to specific devices for action, or pull down the entire dataset to build an analysis (or integrate elsewhere), work with them directly to make known where they should keep an eye—and possibly remediate ASAP.
Secunia Research security advisories deliver reliable, curated and actionable vulnerability intelligence. Put that data to use and share it with your colleagues.
Want to learn more about what’s included in a security advisory from Secunia? Check it out here.






